KlasOS Keel
The Intelligent Edge OS
KlasOS Keel Overview
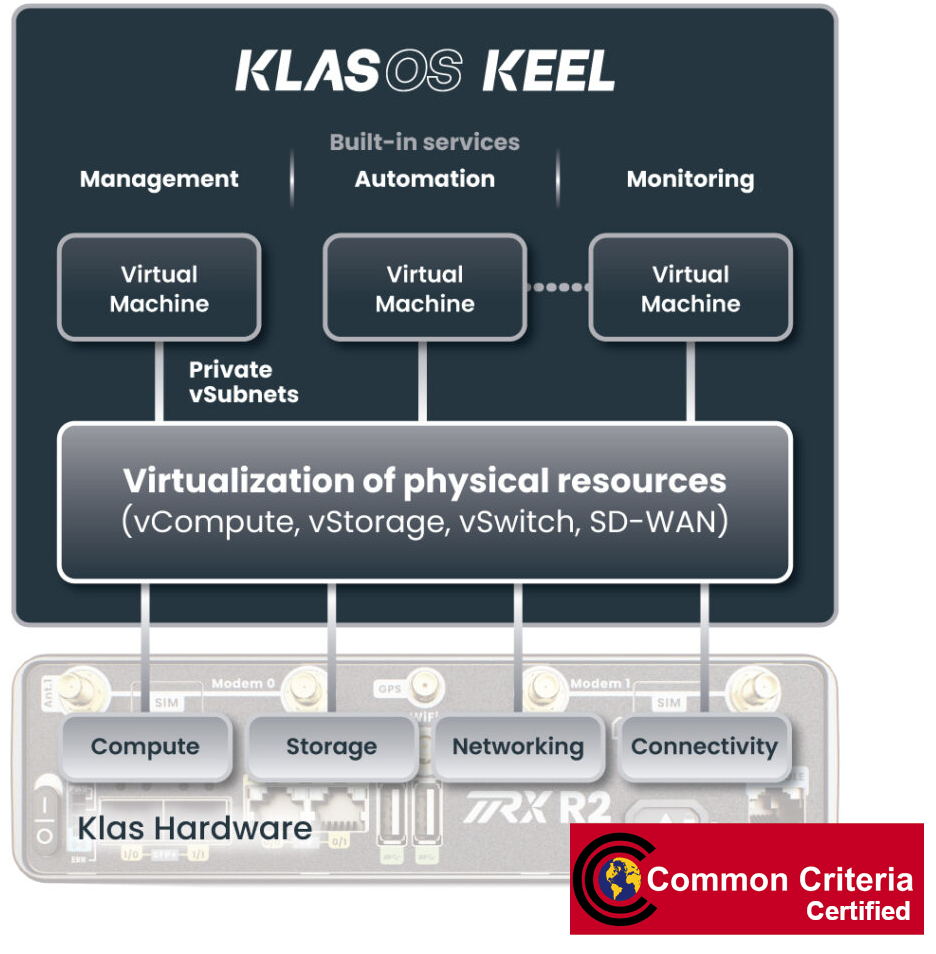
Keel is a lightweight linux based open source OS, with integrated KVM-based hypervisor, routing and virtualized switching, firewall, and SD-WAN capabilities, providing a secure virtualization environment on x86 compute platforms.
The integrated KVM-based hypervisor supports sharing of the modules physical resources of compute, storage, networking, connectivity and pass-through of serial periphery e.g. USB, CAN, MVB to the hosted Virtual Machine.
In addition, Keel supports a secure web based portal, allowing IT admins to control and access their virtual machines without the need to install software on local machines.
Keel is NIAP Common Criteria Certified [CCEVS-VR-VID11436-2024] and is listed as a NSA CSfC component [Traffic filtering firewall].

Keel on Klas modules
Keel ships on a range of Klas modules, such as the TRX R2, TRX R6, VoyagerVM and Voyager m-Series as the default OS.
Keel Functions and Features
The following is a high level overview of supported features and capabilities of Keel and its KVM hypervisor. For a comprehensive overview of Keel please request a demo.
For a technical overview on configuring and using Keel, click on the Helpdesk link under the category. The articles are made public from our in-depth Knowledge Base as part of our online support helpdesk.
| Category | Features |
|---|---|
|
Firewall [Helpdesk Articles] |
|
|
Network and Routing [Helpdesk Articles] |
IPv4/IPv6, DNS, DHCP client/server/relay, NAT, Virtual Router Redundancy Protocol (VRRP), OSPF, BGP, IP SLA (Auto-PACE), DNS, GRE, mGRE, NTP, PIM, Jumbo frame support, Link Aggregation (802.1AX/802.3ad), VLAN (802.1Q) |
|
SD-WAN
[Helpdesk Articles] |
|
|
Virtualization [Helpdesk Articles] |
|
|
Cellular [Helpdesk Articles] |
|
| Wi-Fi |
|
| GPS | GPS relay |
| Management and Monitoring | SNMP, Persistent logging, SSH, Traceroute, ICMP Ping, OneView (VNC web service), Traffic capture, FIPS 140-2 Approved Cryptographic Algorithms |
| Access control / Security | RADIUS, local authentication and authorization, 802.1X Supplicant, TACACS, No direct system access |
Keel Use Cases
Keel delivers the flexibility and ease to deploy multi-tenanted services as hosted VMs at the edge. With integrated routing and virtualized switching capabilities users can quickly and easily create multiple secure and IP segmented networks, with LAN and/or WAN accessibility.
Furthermore, Keel’s integrated SD-WAN capabilities provide prioritization and automated WAN selection and routing of traffic, with support for traffic load balancing over a secure network overlay. Keel SD-WAN eliminates the need for 3rd party VPNs when connecting to virtual private cloud services, or when connecting directly to private networks and servers on-premise.
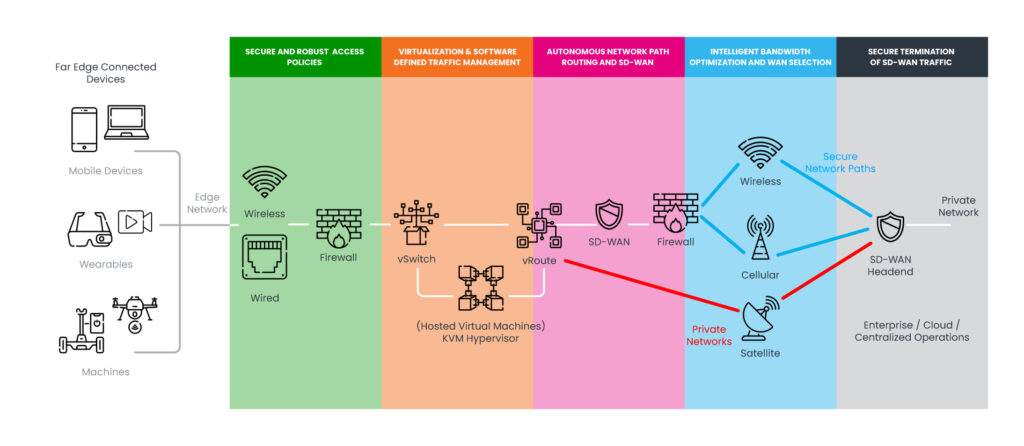
Figure: A topology of Keel software-defined capabilities for end-to-end secure communications.
Use Case - Secure Edge Connectivity
Industry Sector: Automotive
Requirement: Data collection service with secure remote access
- Keel CLI is used to securely upload/update the data collection VM image via SCP.
- Ease of assigning dedicated storage spaces and private IP sub-networks.
- Secure access to the VM using IP ACLs.
- Secure path over a cellular connection with bidirectional access between the users cloud or on-premise server and the edge with Keel SD-WAN.
- Interconnection of two private networks using NAT.
Use Case - Virtualized Multi-tenant Edge
Industry Sector: Government
Requirement: multi-tenanted private data services
- Separated physical resources per hosted tenant.
- Dedicated virtual resources per VM.
- Tenant isolation using network segmentation – dedicated vSwitch, with unique IP subnetworks.
- L3 routing with dedicated physical WAN ports per tenant VM.
- Secure network access with unique IP ACLs per tenant.
- FIPS 140-2 Approved Cryptographic Algorithms
Use Case - IoT Telematics
Industry Sector: Rail
Requirement: high bandwidth data transfers to Virtual Private Cloud (VPC)
- Connects to both ethernet and serial based sensors – CAN, MVB and USB.
- Data pre-processing and tagging with GNSS/GPS meta-data.
- Supports multiple Mobile Network Operators.
- Aggregates all available WAN bandwidth, maximizing data throughput.
Keel Packaging and Certification
Keel is available as a single image (.bin) file, signed with a digital signature for ease of secure updates over the air. Keel is NIAP Common Criteria Certified [CCEVS-VR-VID11436-2024] and is listed as a NSA CSfC component [Traffic filtering firewall].
Keel package differentiators:
- Packaged as a single image file containing the entire operating system.
- Digitally signed package, malformed or malicious images will not load in Klas modules.
- Keel runs in RAM, and is not corrupted by the sudden loss of power.
- Several versions of Keel images can be stored locally on the module for failover or fallback operations.
- Keel comes with integrated driver software supporting multiple cellular and Wi-Fi modems.
`
Discover the advantages of using Keel
Reducing the burden on IT and network professionals with a secure and future-proofed intelligent and secure edge OS.
Lower Cost of
Ownership
Eliminates the need for multiple devices and the complexity of running siloed infrastructure at the edge.
Enhanced
Security
Reduced security exposure to threats that are commonly associated with traditional OS types.
Faster
Deployments
Minimal effort and experience required to deploy the edge, automated configuration for plug-n-play roll outs.
Related Products
Blackrock
Fleet Management Software
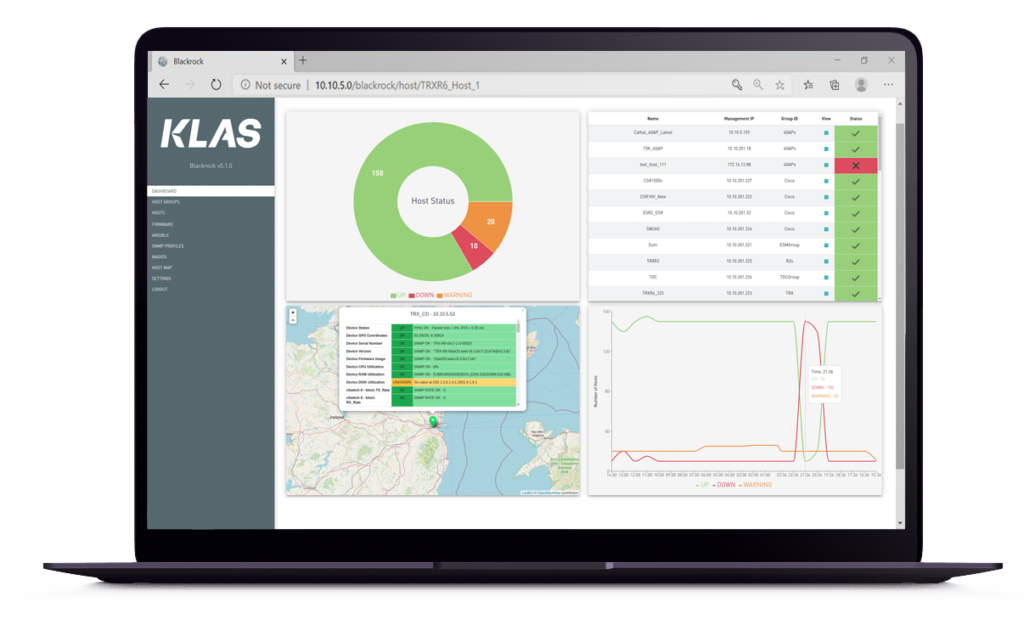
Keel can be directly provisioned or updated using an industry-standard CLI or Web GUI. For large scale provisioning/updates it comes with an Ansible library which can be used by any management solution or as part of the Klas open-source management solution Blackrock.
Blackrock supports remote monitoring of the Keel enabled hardware, guest virtual machines and the sensors that it has access to using standard protocols of SNMP and syslog.